Image Source: Wikipedia.
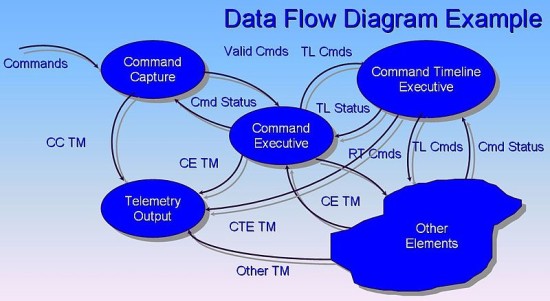
The data flow diagrams demonstrate the way the information is refined by a procedure or a method in relation to the information and production. It is a system of graphics that represent the continuity of knowledge and the changes that are put into practice as the information change type of input and its production. It contributes to the easy and instinctive process in order to define the business systems without putting an emphasis on the inside information on the computers. The data flow diagrams are pleasing yet charming methods because they give whatever is actually done by the users instead of concentrating on what is made or created by the computer systems. These diagrams might get into function for every degree of preoccupying the information. Every level or the degree has greater knowledge continuity and information operative inside information as compared to the preceding level.
The data flow diagram might look like a continuity table or chart but there is a major dissimilarity between the two. These are a magnificent lead for confirming the consistency or agreement of the procedure, layout and forms of the whole system. This happens because of the fact that for making the greater implementation to be victorious, the execution of both procedures and preserving the information is significant.
The collection and arrangement of data that preserves the information in the tables and columns that are being interacted with other columns and tables in the arrangement of data is known as a relational database management system, whereas the database management systems do not contain any such interactions between the tables and columns.
The database management system is accessible in separate and distinct types as a device that is accustomed to handle the collection and arrangement of data. The relational database management system is needed when a majority section of the information is preserved and also well-kept.
One of the few differences also include the fact that the database management system is operated for easier commercial requisitions whereas the relational database management system works with more complicated applications. Regardless the fact that the general idea of the unknown key is advocated by both systems of database but the act of imposing authorities is undertaken by the relational database management system specifically. Furthermore, it is essential and obligatory for the significant sets of information, while on the contrary, the trivial sets are handled by the database management system.
Therefore the complicated diligence of commercial dealings utilizes the relational database management system instead of making use of the database management system.
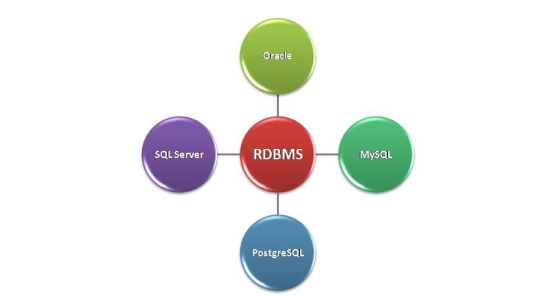
Image Source: kendba.com
The relational database management system is a kind or category of the database management system that preserves the information in the shape of associated tables. The relational database is effective because they demand and need exclusive presumptions related to how the information is associated and and how it will be excerpt from the collection of data that is arranged for ease. As an outcome, the similar collection of data will be displayed in various forms.
A significant characteristic of this relational system is that a solitary collection of data arranged can be stretched through distinct tables. This is different from the database model , in which every collection of data is capable of holding in a solitary table. Nearly, all the partial procedures for the collection of data arranged are relational database management systems. However, the trivial procedures of collections of data and information practice alternate plans and designs that give the lower amount of pliability in proposing inquiries.
The top most creations of relational database management system include Oracle and SQL server also. Most of the fresh collaborative collections of data are currently being produced and handled with the relational database management systems.
A compiler is a plan or a presentation in computer that converts the the origin of the rules and principles transcripts in a the form of a system of symbols and and rules that are used for communication with or between computers. The highly usual and conventional purpose for expecting the alteration of the origin of the rules and laws is to produce a feasible yet workable system of services and opportunities.
Its inclined to fulfill either a few or the entire list of functions that include a study or interpretation related to lexicon to perform preliminary processing on the data, to examine the information closely, interpretation according to the science of semantics, a series of rules of conduct or procedure and the process used to make a system of rules and laws.
In order to reduce the complexity of the plan of a compiler and the system of formation, the compiler is carried out in several stages. Furthermore, it might also contain stages that are as effective and functional as possible in order to make effective and successfully designed plans or systems.
Whenever a program has been chosen for the execution, the system would bring the virtual storage into it. It then divides it to about 4KB pages and transfer the pages in the central storage or the execution. To the programmer, the whole program seems to occupy the storage space at all times. Usually, not all of the pages of the program are being necessary in the central storage and the entire pages placed on its do not mainly occupy much of the space.
On the other hand, the page, the frame as well as the slot are similar in sizes, which is 4 kilobytes. The active virtual storage page mainly resides in the central storage, which is the frame. The page of the virtual storage, which has become inactive mainly dwells in the auxiliary storage slot. You could always consider looking up for figures that shows mainly the relationship of frames, slots as well as pages.
In order for you to comprehend how paging really works, you can assume that the DAT encounters some sort of a table entry page that is invalid throughout the translation of the address, indicating that the needed page, which is not in the central storage frame. For one to resolve the fault page, the system has to bring the page in from the auxiliary storage. The only thing is that, it should locate the available central storage firm fist. Understanding such things could help you know what paging really is.
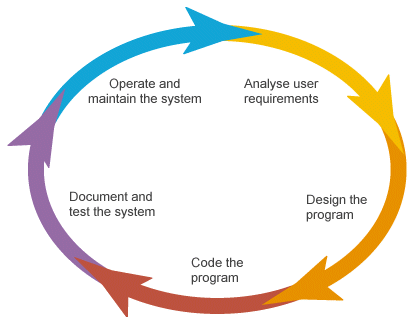
Image Source: blog.teachbook.com.au
Every single stage of the software development life cycle creates products that are needed by the adjacent stage of this cycle. The several phases of the software development life cycle include a perquisite collection or accumulation and examination, under which the commercial necessities are collected. This particular stage is the supreme center of emphasis for all those who deal and directs the plan as well as the ones holding shares.
The next stage of the software development life cycle is related to the construction of the structure and the programs, which are created according to the necessities and the already mentioned details. It prepares the information and material that might be required for the upcoming stage of this cycle.
Furthermore, on getting the files and information on the classification, the functioning is shared out into the units of measurement and this is when the basic process of a systematically arranged and comprehensive collection of laws takes place. This is considered as the most extended stage of the software development life cycle.
After producing the comprehensive collection of laws, it undergoes a trial while comparing all the demands and needs in order to assure that the product is properly fulfilling the requirements. Therefore, having a favorable outcome allows the item to be dispatched to the client.
Do you always find yourself searching on the internet. It is actually amazing thinking about the way on how the internet really works. It simply feels like magic the way in which a person could connect to the internet, make their researches, watch out for videos and more. How can this be a thing possible? Well, thanks to the TCP/IP or the Transmission Control Protocol/Internet Protocol.
The TCP/IP have been developed in the year 1978, which has been also driven by Bob Kahn and Vint Cerf. These days, the TCP/IP is also a useful kind of language that governs the communications among the entire computers that are also on the Internet. On the other hand, the TCP/IP is a separate kind of protocols, though they are being used together. The standard of Internet Protocol simply dictates the way on how packets of the information are being set out for over the networks. The internet protocol has its packet-addressing method that mainly lets any sort of computer on the Internet and forward a packet into another computer which is mainly a step or something that is closer into the recipient of the packet.
Moreover, the TCP also makes it sure that the data transmission is also reliable around the networks connected to the Internet.
Have you always connected your net accessible gadgets to the internet? You must have heard IP and already know that it means Internet Protocol. However, do you really have any idea about what it really is? IP is the primary protocol of the network being used online. It has been developed in the year 1970. IP also supports the unique addressing for the computers on a certain network. Most of these networks are using Internet Protocol in version 4 with the standard featuring the addresses that are about 16 bytes in length.
The data on the Internet Protocol network is being organized into the packets. Every IP Packet mainly includes both of the header which is used for specifying the destination, source and any other information regarding the data as well as the data of the message itself. Moreover, the IP simply functions of the third layer of the OSI Model. Thus, it could run on the top of various interfaces of data including WI-Fi and Ethernet. It only means that Internet Protocol is one of the essential matters when it comes to connecting to the internet. Moreover, upon the internet and any other networks, Internet Protocol is frequently used together with the TCP or the Transport Control Protocol and known together as TCP/IP.
So, what are the Network Topologies? In simple sense, they refer to as the network layout and how the varied nodes in the network are connected to each and everyone and on how they communicate as well. Mesh Topology is a kind of Network Topologies in which in a mesh network, the devices are being connected with a whole lot of redundant interconnections in between the network nodes. There are actually two kinds of mesh topologies, here are those:
• Full Mesh – it takes place when each and every node has their own circuit that connects each and every other node into the network. The full mesh topology is somewhat an expensive one to implement, yet it yields a wider redundancy amount. Thus, in the event that one of the nodes had failed, the network traffic could be directed to any other kinds of nodes. Usually, full mesh is reserved only for the networks that serves as the backbone.
• Partial Mesh- it is somewhat less expensive to implement and it only yields very less sort of redundancy than the latter. With such, some of the nodes are being organized in complete scheme, yet the others are only connected to one or two in a certain network.
Knowing more about the essence of Network Topologies could surely help one out.
Simply imagine the number of people who are communicating across the world. They are using up various languages and different machines and even uses up different software in order to transmit data. If there are no standards, communication around the world would never be possible. Well, one of the tools being used for transmitting data is the protocol? So, what is the protocol? It is actually used for the reliable transmission of data for every the network. The HTTP or the HyperText Transfer Protocol being used for transmitting as well as displaying the information in the form of web pages across the browsers on the internet.
On the other hand, there are three kinds of Protocol, here are those:
• TCP- known as the Transmission Control Protocol that uses a good set of rules in order to exchange the messages with any other internet points at the packet level of information.
• IP- known as Internet Protocol that uses a good set of rules in order to send and receive messages at the address level of the internet.
• FTP or HTTP- stands for File Transfer Protocol or Hypertext Transfer Protocol that has their own defined set of rules to use with the corresponding programs anywhere else on the net.
Knowing the different types of protocol could help you understand about on how they are being used.
Page 1 of 2412345...1020...»Last » 


