Databases Questions and Answers
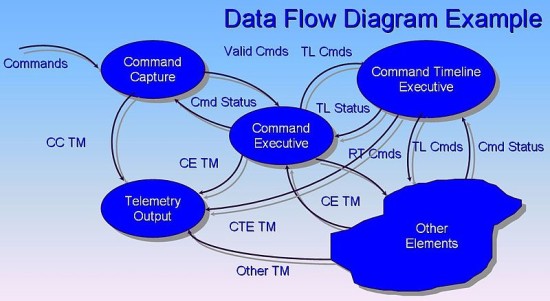
Image Source: Wikipedia.
The data flow diagrams demonstrate the way the information is refined by a procedure or a method in relation to the information and production. It is a system of graphics that represent the continuity of knowledge and the changes that are put into practice as the information change type of input and its production. It contributes to the easy and instinctive process in order to define the business systems without putting an emphasis on the inside information on the computers. The data flow diagrams are pleasing yet charming methods because they give whatever is actually done by the users instead of concentrating on what is made or created by the computer systems. These diagrams might get into function for every degree of preoccupying the information. Every level or the degree has greater knowledge continuity and information operative inside information as compared to the preceding level.
The data flow diagram might look like a continuity table or chart but there is a major dissimilarity between the two. These are a magnificent lead for confirming the consistency or agreement of the procedure, layout and forms of the whole system. This happens because of the fact that for making the greater implementation to be victorious, the execution of both procedures and preserving the information is significant.
The collection and arrangement of data that preserves the information in the tables and columns that are being interacted with other columns and tables in the arrangement of data is known as a relational database management system, whereas the database management systems do not contain any such interactions between the tables and columns.
The database management system is accessible in separate and distinct types as a device that is accustomed to handle the collection and arrangement of data. The relational database management system is needed when a majority section of the information is preserved and also well-kept.
One of the few differences also include the fact that the database management system is operated for easier commercial requisitions whereas the relational database management system works with more complicated applications. Regardless the fact that the general idea of the unknown key is advocated by both systems of database but the act of imposing authorities is undertaken by the relational database management system specifically. Furthermore, it is essential and obligatory for the significant sets of information, while on the contrary, the trivial sets are handled by the database management system.
Therefore the complicated diligence of commercial dealings utilizes the relational database management system instead of making use of the database management system.
Image Source: kendba.com
The relational database management system is a kind or category of the database management system that preserves the information in the shape of associated tables. The relational database is effective because they demand and need exclusive presumptions related to how the information is associated and and how it will be excerpt from the collection of data that is arranged for ease. As an outcome, the similar collection of data will be displayed in various forms.
A significant characteristic of this relational system is that a solitary collection of data arranged can be stretched through distinct tables. This is different from the database model , in which every collection of data is capable of holding in a solitary table. Nearly, all the partial procedures for the collection of data arranged are relational database management systems. However, the trivial procedures of collections of data and information practice alternate plans and designs that give the lower amount of pliability in proposing inquiries.
The top most creations of relational database management system include Oracle and SQL server also. Most of the fresh collaborative collections of data are currently being produced and handled with the relational database management systems.
Do you know what a splash page is? Well, it is the website page in which the user sees right before getting into the option of continuing into the main content of the website. A splash page is being used to promote a certain company, product or services or being used to inform all of the users about the kind of browser or software needed in order to see the entire pages of the website. Some of the splash pages would actually bring up the user into the main website in an automatic way and some would need the user to click up on the link that would surely load the main page. Some of the advantages of splash pages are:
• Loads fast and they get the entire information in a faster way even without the need to scroll.
• The splash pages make it sure that all of your readers would be able to see your flash or animation even once.
• Splash pages are a good way in showing off your work just like how portfolio does it.
• Splash pages would let your readers to choose the website technology that fits into them.
Splash pages is a good thing that you could have for your website, not to mention that it could also be created by you.
In the vernacular of online advertising ad internet, the squeeze page is a kind of page on the web containing information that will definitely interest the targeted readers of every marketer. These squeeze pages are being designed to get the name and the email address details of the reader by mainly encouraging the users to choose an email list in order to receive more information regarding the topic. The marketers will then collect the emails and information which is based upon the information. This is taken in order to follow up at a much later date.
These days, there is some debate regarding the actual definition of these squeeze pages. Some even consider landing ages that would offer up additional hyperlinks to the information and email that are in being signed up to be the squeeze page. However, some people who are standing in the same industry only believe those pages that contain an email sign up are also squeeze pages. In a simple sense, the best definition about what squeeze pages really are is that, it is a page being designed to get the email addresses and names, with the Opt-in form, wherein the potential customer should fill in.
Thrashing is the operation of dumping memory when the system is used at its maximum capacity, to transfer data between the physical and virtual memory. For example, if the user runs multiple tasks at the same time, the operations of exchanging data between the hard disk and the virtual memory might be demanding for the computer, and in this case, when the computer “cleans” the virtual memory from unneeded data, the process is called trashing. This phenomenon appears only if the virtual memory is overworked; ad the instability of the system is common in those cases.
Trashing might lead to a slow computer. Trashing is also a harmful operation for the hard drive, as it is used at its maximum capacity. If trashing occurs often, it will eventually lead to a hard drive crash.
There are several methods that can be used to avoid trashing:
1 – Increasing the RAM capacity of the computer.
2 – Running a smaller number of programs at the same time.
3 – Increasing the number of power of BUS connections that are responsible for the data exchange process.
4 – Reinstalling the operating system, or installing a performing one. However, if the new OS is too demanding for the computer, the process of trashing might be more severe, and it could bring more problems to the system.
Serialization is the modifying process of a structure of modeling data, made with the purpose of integrating the respective concept into other databases. It is important to find the right format, so the new structure would be fully integrated in the database. The simplest and easiest way of understanding serialization is to take the example of memory buffering, or network connections. A piece of a program is inserted into the memory buffer, with the purpose of integrating the respective structure into another structure later.
This secondary structure could be another program, another computer, or another network node. Serialization is used to create an identical clone with the initial program, and to adapt it to fit into the new structure. However, for complex objects, it is impossible to create the perfect clone, therefore there are secondary methods used to create the clone that fits the secondary system. You will find this process under the name deflating, but it is basically the same process: the procedure of extracting data from a string of binary codes, as a method to describe objects, with the purpose of placing the respective objects into a new compatible structure. It is a method of distributing objects, which is commonly used to improve programs and software, and to create updated versions of the respective codes.
Do you know what data dictionary is? Well, it is a file defining the basic organization of the database. A data dictionary mainly contains a good list of entire files in the database alone. The number of records on every file as well as the types and the name of every field. Most of the database management systems mainly keep up the data dictionary being hidden from the users in order to prevent it from destroying the entire contents in an accidental manner.
At some point, the database applications could be easily done in a simpler way if you only uphold a body of data reciting your tables. Each of the single programming tasks in the database application has to know something regarding the tables in which it is working with. Thus, every program in the framework and other programs in the application alone could actually benefit from the central information store regarding the database.
Moreover, the term data dictionary is being used by many people. This way, they could denote the separate set of the tables describing the application tables. The data dictionary containing all of this information as the types, column names as well as sizes, yet descriptive information just like the foreign keys, primary keys, titles and the captions for the user interface regarding how to display the field.
The purpose of hashing is to construct, explore or erase from the record or a table. The main concept or method involved in hashing is to catch a an area or a domain in a document, which is called a key. It transforms the key using a constant procedure into a numerical use, that is named as the hash key. It describes the situation for either keeping or searching a component in the table.
The most frequent way of discovering the hash key is the separation process or technique of hashing. It has a specific formula that makes the processing possible. Under the process, the option of using the hash as well as focusing the dimensions of the table are required to focus on observantly. The users should also make themselves aware of the fact that the keys are not invariably numeric. As a matter of fact, it is usually as a string.
This procedure is mainly a sensible and appropriate policy except for the fact that the key has certain objectionable attributes. The process of hashing includes calculating the location inwardly the orderly arrangement. It also contains numerous fully known activities as well. It is also operated in various encoding algorithms.
The Unified Modeling Language or the UML is a fast kind of skill when it comes to virtually anyone who is involved in the project of software. The requirements analysts, architects, software developers, database professionals, UI designers, project managers as well as designers are definitely asked to consume and create specifications that are written in the UML.
On the other hand, the UML for the Managers is definitely a 6-part kind of ebook explaining what UML really is and what it could be used for in both business change as well as software development projects. Thus, it explains clearly the concepts just like the enterprise, business modelling, architecture as well as object oriented analysis as well as the design without bogging down the reader in a certain kind of technical detail in which a programmer could only understand.
Moreover, it also shows you the possible upcoming of modeling, wherein the whole application could be made from those of the high-level UML models and highlights the best practices or adopting the UML into your business or organization. Interns of event in the UML, it is a distinguished incidence at a certain time. At some point, events could, yet they do not essentially cause state evolutions for a certain state to another state machine being represented by the machine diagrams.


