Inheritance mainly suggests a certain object to be able to inherit the characteristics from any other objects. In a more concrete terms, the object is something that could pass on its state as well as behaviors to the children. For the inheritance to work, the objects need to have characteristics that are common with each other.
For instance, simply put that you make a class known as the “human”, which is representing your physical characteristics. Thus, it is a generic class that could surely represent you. It is a state that simply keeps a good track of the good things just like he number of arms, legs as well as the blood type. It has the behaviors of sleeping, walking and eating. The “human” is also a good one for getting the entire sense of what makes everyone to be the same, yet if you could not, simply tell them about the differences. If that’s the case, they could simply make new types of classes known as the Man and the Woman. The state as well as the behaviors of such classes would definitely differ from each other in many ways except for those that they inherit from the HUMAN.
It only means that inheritance mainly lets you encompass the class’ state of the parent as well as the behavior in the child. So, the class of the child could then extend the state as well as the behaviors reflecting the differences that it represents.
When using ASP.NET in developing a website, the master page is a feature enabling the developer to define the common structure as well as internet markup elements for your website. It actually includes footers, headers, style definitions or even navigation bars. The master page could be shared up by any pages into your website and these are known as the content pages. The only thing is that, it will have the need to remove the duplicate code for the shared elements that are into your website.
Moreover, the master page is a very useful kind of mechanism in the ASP.NET in order to make a uniform layout for the entire pages. It could simply contain about one or more placeholders where the actual content is being restored. The master page will always be the same and it will provide a good kind of scaffolding for the entire pages that you have. For the reason that the master page is always similar, it mainly defines the feel and the look of the entire pages upon your website. The rest is being saved into the content placeholders that would merge the master pages and the entire page. This is simply how master pages work on a developer’s point of view.
Systolic array is a specific type of parallel computing. An organization of processors in an array where information flows contemporaneously crossways the array amongst neighbors, generally with diverse information flowing in diverse directions is known as systolic array.
Systolic array is a grid like arrangement of particular processing rudiments that processes information just as a n-dimensional pipeline. Contrary to a pipeline though, the input data as well as fractional outcomes stream through the array. It generally has an excessive rate of input/output and are suitable for comprehensive parallel operations. Furthermore, information can run in a systolic pattern at various speeds in various directions.
In systolic array numerous processors are connected by short wires which results in improved speed as compared to other types of parallelism which lose speed through their connection. Every processor at every phase obtains information from one or more neighbors, processes it and, in the next phase, produces outcome in the contrary direction.
Some special features of systolic array are its exceptionally high speed, effortlessly scalable structural design and its ability to perform various tasks which single processor machines cannot accomplish. But some of the drawbacks are that it is very expensive, hard to develop and implement and not required for most of the applications due to its highly specialized nature.
In an operating system, the task of the scheduler is to administer the workload of the processor in order to keep a balance in the amount of work for the processor in such a way that the throughput is maximized. There are different algorithms for this task. One of them is First Come First Served (FCFS) algorithm. FCFS is one of the easiest scheduling algorithms. In this algorithm, the scheduler assigns the processor tasks in the same order as they come. This method can be understood as a daily life queue. The first task arrived will be processed first and the task coming after that will be joining the queue by the end and so on.
The good thing about this algorithm is that it is easy to implement. While one of the negative points is that it is non-preemptive – means when a task is assigned to the processor it can’t be interrupted during the processing while in other “preemptive algorithms” the processing of task/process can be interrupted on the basis of priority and/or time. Another drawback is that parallel processing is not allowed.
Nowadays this algorithm is not implemented independently (due to slow response time) but still it is part of many other scheduling algorithms.
Do you know what Ben’s Network is and how it works? Well, with Ben’s Network service, they truly appreciate that not all of the companies mainly have he same need when it comes to their IT division. Some actually need a full time tech on-site and others just require a little courtesy once in a week. Whatever you need, they are able to do as much or as little, depending upon what you truly need.
On the other hand, for the larger companies, they are offering the on-site technicians to handle the needs and the software updates of their users. With the backing of the other root of the technicians as well as computer upgrades on the larger scale, they are sure enough to help you with everything that you need. They even assist desk to work with the users for faster resolution and rental computers and printers whenever your unit is in need of repair.
For those of the medium sized companies, they are offering great assistance for the employees and go back to it together with the tools in order to keep you running with great options in terms of help desk, computer as well as printer rentals. The monthly service plan on the equipment as well as upgrade and even rollout testing for the compatibility of the pre-upgrade.
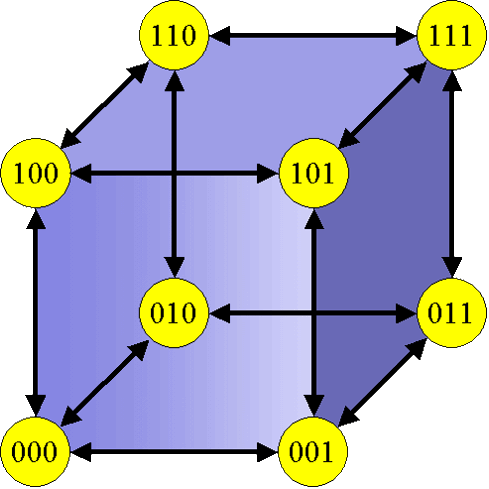
Image Source: cs.virginia.edu
Developments in hardware technology have made it feasible to fabricate a large scale multiprocessor system which holds tens of thousands of processors. One vital measure on planning such a multiprocessor system is to establish the topology of the interconnection, because the system operation is extensively affected by the network topology.
Generally when a n-dimensional grid network is linked circularly in more than a single dimension, the consequential network topology is a torus, and the resultant network is known as toroidal. When the number of nodes along each dimension of a toroidal network is two, the consequential network is described as a hypercube.
The binary n-cube, additionally known as the hypercube network has been confirmed as an extremely powerful topology. Hypercube is the most extensively benefited from topology for the reason that it offers small diameter, that is the greatest number of links (or hops) a message has to pass through to achieve its ultimate destination between any two nodes. It also implants a variety of interconnection networks. For exceptionally huge systems though, the number of links required by the hypercube could turn out to be prohibitively large.
The main limitation of the hypercube network is its lack of scalability, which restricts its application in constructing bulky systems out of small size systems with modest of alterations in its configuration.
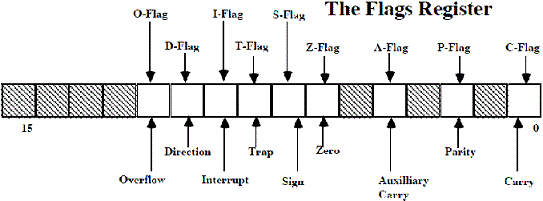
Image source: 8085projects.info
A flag register is an alternate that signify a few situations that are created by the style and technique of an imparted knowledge or conducts inevitable functions of EU. The flag register is 16 chips elongated. It does not carry a single digit, in fact it has a set of chips. It terminates the circulating region of the central processing unit. They are altered mechanically by the central processing unit after the exact and absolute functioning. This will permit to consider the kind of the outcome, and to discover the perquisites in order to shift the power to the rest of the portions of the program. Normally, these registers are not instantly visible or acquired.
Flag registers are chips that give guidance related to the reasonable situations that persisted as an outcome of the result of a performance that took place according to the imparted knowledge. This enables the supervened information to process consequently. There are various categories of flags that are processed in their own ways. The flags activate and deactivate indisputable functions of the central processing unit. Due to the fact that all kinds of flag registers are elongated having 16 chips, they can hold the information and data in the space of capacity storage within the purview of 64k units or bits.
The Expert System is a kind of computer program simulating the behavior as well as the judgement of the human or the organization with expert experience as well as knowledge in a certain field. Usually, this kind of system mainly contains a good knowledge base with all of the accumulated experience and also a set of rules to be used when applying the base of the knowledge to every situation being described in the program. The sophisticated expert systems could be easily enhanced with the additions to the base of the knowledge or even to the set of the rules.
On the other hand, while any other conventional programming language could be used in order to build up a base of knowledge, the shell of the expert system will simplify the procedure of creating a good knowledge base. Actually, it is the shell that processes the entire information entered by the user. They will then relate it to the concepts being contained in the knowledge base providing great assessment or solution for certain problems. So, the shell of the expert system gives a good layer in between the user interface as well as computer operating system in order to manage both of the input and output of the data.
Do you know what system analysis is? Well, as its name states, it is the analysis of a system, which mainly include organizations as well as businesses. This could be systems of financial systems, communication, and manufacturing systems and more. Basically, these are the systems making the business or the organization to work.
On the other hand, a person doing the work of analyzing the systems, they are known as the Systems Analyst. At some point, analysts are being employed by the organizations of the businesses to assist you in improving their systems and to become far more efficient and for the businesses and become a lot more profitable. Moreover, here are some of the roles of being a system analyst:
• Analyzing the existing business operations as well as the existing information systems, whether it is computerized or not.
• Study the trends available in the technology.
• Study the trends in the business and has to be aware of the competitors’ together with the technological exploitation.
• They propose an alternative solution to the problems of the business and choose a good solution as well as justifying the selection.
If you would like to be a system analyst, it would be a good thing for you to have the ability of solving problems and understanding the possibilities of the computer technology.
The TCP/IP is one of the highly used network protocols, these days. However, do you have any idea about what network protocol really is? Well, protocol is like a language being used to make two computers talk to each other. Just like in the real world, if ever they don’t talk the same language, they are not able to communicate.
On the other hand, the TCP/IP is not actually a protocol, yet it is a set of protocol. It is actually known as the Protocol stack, as what it has been commonly known. For instance, it already refers to two variable protocols, the TCP an the IP. Moreover, on the internet layer, you have the Internet Protocol or the IP that gets the packets being received from the Transport Layer and add up virtual address information, just like adding the computer address that is sending the data and the address of the computer that will then receive the data. All of these virtual addresses are known as the IP Addresses. After then, the packet will be sent into the lower layer, called as the Network Interface. With this layer, the packets will be known as the datagrams. The packets that are also transmitted over the network are then known as the frames.


